Webhacking.kr 5번 문제 풀이
5번 문제다.

로그인 버튼을 눌러서 들어가면 id랑 pw를 입력하라는 창이 뜬다.

가볍게 injection 공격을 했는데

맨 위에 Wrong password라는 말이 뜬다.

일단 다시 메인으로 들어와서 join 버튼을 눌러 봤는데, Access_Denied 라고 한다.
/mem/login.php 페이지는 로그인 페이지니까 혹시 join.php도 있지 않을까 해서 입력해봤는데

bye라고 함;
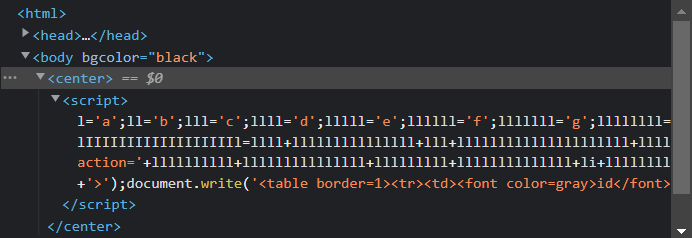
그대신 스크립트로 어떤 코드가 적혀있었다!
l='a';ll='b';lll='c';llll='d';lllll='e';llllll='f';lllllll='g';llllllll='h';lllllllll='i';llllllllll='j';lllllllllll='k';llllllllllll='l';lllllllllllll='m';llllllllllllll='n';lllllllllllllll='o';llllllllllllllll='p';lllllllllllllllll='q';llllllllllllllllll='r';lllllllllllllllllll='s';llllllllllllllllllll='t';lllllllllllllllllllll='u';llllllllllllllllllllll='v';lllllllllllllllllllllll='w';llllllllllllllllllllllll='x';lllllllllllllllllllllllll='y';llllllllllllllllllllllllll='z';I='1';II='2';III='3';IIII='4';IIIII='5';IIIIII='6';IIIIIII='7';IIIIIIII='8';IIIIIIIII='9';IIIIIIIIII='0';li='.';ii='<';iii='>';lIllIllIllIllIllIllIllIllIllIl=lllllllllllllll+llllllllllll+llll+llllllllllllllllllllllllll+lllllllllllllll+lllllllllllll+ll+lllllllll+lllll; lIIIIIIIIIIIIIIIIIIl=llll+lllllllllllllll+lll+lllllllllllllllllllll+lllllllllllll+lllll+llllllllllllll+llllllllllllllllllll+li+lll+lllllllllllllll+lllllllllllllll+lllllllllll+lllllllll+lllll;if(eval(lIIIIIIIIIIIIIIIIIIl).indexOf(lIllIllIllIllIllIllIllIllIllIl)==-1) {alert('bye');throw "stop";}if(eval(llll+lllllllllllllll+lll+lllllllllllllllllllll+lllllllllllll+lllll+llllllllllllll+llllllllllllllllllll+li+'U'+'R'+'L').indexOf(lllllllllllll+lllllllllllllll+llll+lllll+'='+I)==-1){alert('access_denied');throw "stop";}else{document.write('<font size=2 color=white>Join</font><p>');document.write('.<p>.<p>.<p>.<p>.<p>');document.write('<form method=post action='+llllllllll+lllllllllllllll+lllllllll+llllllllllllll+li+llllllllllllllll+llllllll+llllllllllllllll +'>');document.write('<table border=1><tr><td><font color=gray>id</font></td><td><input type=text name='+lllllllll+llll+' maxlength=20></td></tr>');document.write('<tr><td><font color=gray>pass</font></td><td><input type=text name='+llllllllllllllll+lllllllllllllllllllllll+'></td></tr>');document.write('<tr align=center><td colspan=2><input type=submit></td></tr></form></table>');}
뭔가 난독화된 스크립트 같은데.. 자바스크립트 난독화된걸 해독화할 수 있는 프로그램이 있는지 검색해봤다.
Javascript Unpacker Tool - Strictly Software
This Javascript unpacker tool has now been upgraded to allow it to unpack multiple eval statements. So if your packed code has itself been packed a few times it will loop through until it finds the original source code. If you want to test this multiple ev
www.strictly-software.com
해당 사이트를 찾았는데 https 연결이 안된 곳이라,,,, 어쨌든 이걸 사용했다

l = 'a';
ll = 'b';
lll = 'c';
llll = 'd';
lllll = 'e';
llllll = 'f';
lllllll = 'g';
llllllll = 'h';
lllllllll = 'i';
llllllllll = 'j';
lllllllllll = 'k';
llllllllllll = 'l';
lllllllllllll = 'm';
llllllllllllll = 'n';
lllllllllllllll = 'o';
llllllllllllllll = 'p';
lllllllllllllllll = 'q';
llllllllllllllllll = 'r';
lllllllllllllllllll = 's';
llllllllllllllllllll = 't';
lllllllllllllllllllll = 'u';
llllllllllllllllllllll = 'v';
lllllllllllllllllllllll = 'w';
llllllllllllllllllllllll = 'x';
lllllllllllllllllllllllll = 'y';
llllllllllllllllllllllllll = 'z';
I = '1';
II = '2';
III = '3';
IIII = '4';
IIIII = '5';
IIIIII = '6';
IIIIIII = '7';
IIIIIIII = '8';
IIIIIIIII = '9';
IIIIIIIIII = '0';
li = '.';
ii = '<';
iii = '>';
lIllIllIllIllIllIllIllIllIllIl = lllllllllllllll + llllllllllll + llll + llllllllllllllllllllllllll + lllllllllllllll + lllllllllllll + ll + lllllllll + lllll;
lIIIIIIIIIIIIIIIIIIl = llll + lllllllllllllll + lll + lllllllllllllllllllll + lllllllllllll + lllll + llllllllllllll + llllllllllllllllllll + li + lll + lllllllllllllll + lllllllllllllll + lllllllllll + lllllllll + lllll;
if (eval(lIIIIIIIIIIIIIIIIIIl).indexOf(lIllIllIllIllIllIllIllIllIllIl) == -1) {
alert('bye');
throw "stop";
}
if (eval(llll + lllllllllllllll + lll + lllllllllllllllllllll + lllllllllllll + lllll + llllllllllllll + llllllllllllllllllll + li + 'U' + 'R' + 'L').indexOf(lllllllllllll + lllllllllllllll + llll + lllll + '=' + I) == -1) {
alert('access_denied');
throw "stop";
} else {
document.write('<font size=2 color=white>Join</font><p>');
document.write('.<p>.<p>.<p>.<p>.<p>');
document.write('<form method=post action=' + llllllllll + lllllllllllllll + lllllllll + llllllllllllll + li + llllllllllllllll + llllllll + llllllllllllllll + '>');
document.write('<table border=1><tr><td><font color=gray>id</font></td><td><input type=text name=' + lllllllll + llll + ' maxlength=20></td></tr>');
document.write('<tr><td><font color=gray>pass</font></td><td><input type=text name=' + llllllllllllllll + lllllllllllllllllllllll + '></td></tr>');
document.write('<tr align=center><td colspan=2><input type=submit></td></tr></form></table>');
}
해독은 안된거 같고 그냥 예쁘게 정리해준거 같음
이번에 처음 알게된건데, 개발자도구 console에 이 부분을 입력해주면 해석을 해준다.

이런식으로..
if (eval(document.cookie).indexOf(oldzombie) == -1) {
alert('bye');
throw "stop";
}
if (eval(document.URL).indexOf(mode=1) == -1) {
alert('access_denied');
throw "stop";
} else {
document.write('<font size=2 color=white>Join</font><p>');
document.write('.<p>.<p>.<p>.<p>.<p>');
document.write('<form method=post action= join.php >');
document.write('<table border=1><tr><td><font color=gray>id</font></td><td><input type=text name=id maxlength=20></td></tr>');
document.write('<tr><td><font color=gray>pass</font></td><td><input type=text name=pw></td></tr>');
document.write('<tr align=center><td colspan=2><input type=submit></td></tr></form></table>');
}
정리하면 다음과 같다. 해석을 100%할 순 없지만 맨 윗줄을 보면 document.cookie, 즉 oldzombie라는 cookie 값이 아니면 bye를 반환하고 있었던 것이다. 그럼 cookie 값을 oldzombie로 바꾸면 어떻게 될까?


bye대신 access_denied가 뜬다. 맨 위 코드에 cookie관련 코드가 적혀있었다면 그 아래엔 URL에 관한 내용이 적혀있었는데, indexOf라는게 특정 문자열을 찾고 그 문자열이 나타내는 첫번째 위치를 반환다는 것이다. 근데 mode=1은... 뭐지

시험 삼아 URL 창에서 맨 뒤에 mode=1을 입력했는데

가입창이 떴다;
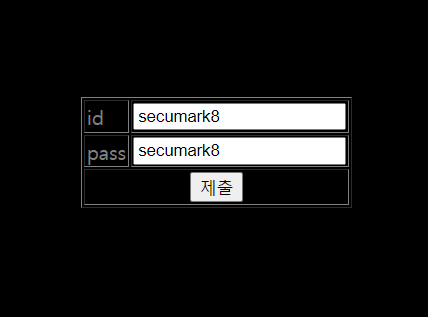
id와 password를 동일하게 secumark8로 지정했다

성공적으로 등록됨. 그럼 다시 login창으로 가서 로그인해볼까

ㅋ
admin으로 로그인하라고 함;
sql injection으로 이것저것 공격했는데 잘 안돼서 burp suite을 켜봤다.
하,, 고민하다가 다른 방법을 알아냈다.

처음엔 admin%20이라고 했는데 아무리 해도 안돼서 검색해보니 널 문자도 넣어야 해결되는 것으로 보인다.


성공

로그인할때도 burp suite 이용해서 admin%20%00로 접속했다.

엥 언제 풀렸담
문제 해결.. 조금 어려웠다.